Product Overview
Product Overview
The database encryption and access control system is a reinforced product that enhances database system and data security. It has functions such as sensitive data encryption and decryption, permission control, complete transparency, decentralized management, and security auditing. It can prevent data theft from internal high privileged users, external attacks, and data leakage caused by disk and tape theft, ensuring the confidentiality and integrity of data.
 Features
Features
 Dynamic encryption and decryption:The encryption and decryption function enables intelligent real-time dynamic encryption and decryption of data stored in the database, without the need for human intervention, fully realizing secure storage and use of data, and preventing information from being classified. This not only saves users time, but also achieves the goal of protecting files. As long as the user has read and write operations on encrypted data, the encrypted data will be automatically encrypted or decrypted, and the user will not feel the existence of the encryption and decryption process.
Dynamic encryption and decryption:The encryption and decryption function enables intelligent real-time dynamic encryption and decryption of data stored in the database, without the need for human intervention, fully realizing secure storage and use of data, and preventing information from being classified. This not only saves users time, but also achieves the goal of protecting files. As long as the user has read and write operations on encrypted data, the encrypted data will be automatically encrypted or decrypted, and the user will not feel the existence of the encryption and decryption process.
 Cipher index:To achieve rapid querying, database files need to establish some indexes. Generally speaking, the establishment and application of indexes must be in plaintext state, otherwise the function of indexes will be lost. After data encryption, the plaintext index will lose its function, resulting in the need to decrypt all data once even if only one data is queried, which undoubtedly increases the query time. The system has patented technology for ciphertext indexing, which enables query operations to retrieve corresponding data without decrypting all data, greatly improving the speed of ciphertext queries.
Cipher index:To achieve rapid querying, database files need to establish some indexes. Generally speaking, the establishment and application of indexes must be in plaintext state, otherwise the function of indexes will be lost. After data encryption, the plaintext index will lose its function, resulting in the need to decrypt all data once even if only one data is queried, which undoubtedly increases the query time. The system has patented technology for ciphertext indexing, which enables query operations to retrieve corresponding data without decrypting all data, greatly improving the speed of ciphertext queries.
 Multi level key technology:Each field has a different, independent, and unique column key, which controls the encryption and decryption of the field. All column keys are generated by the master key, which controls the encryption and decryption of the column keys. The master key is stored in hardware to ensure it is not stolen or destroyed, while the column key is stored in an encrypted database. By using dual key technology, encrypted data is guaranteed not to be cracked, increasing security.
Multi level key technology:Each field has a different, independent, and unique column key, which controls the encryption and decryption of the field. All column keys are generated by the master key, which controls the encryption and decryption of the column keys. The master key is stored in hardware to ensure it is not stolen or destroyed, while the column key is stored in an encrypted database. By using dual key technology, encrypted data is guaranteed not to be cracked, increasing security.
 Transparent encryption:The encrypted data is completely transparent to legitimate applications and client tools for access. Applications or personnel cannot feel the encryption and decryption process when accessing encrypted data, just like the way plaintext data is accessed. While ensuring data security, it will not change the access habits of applications or personnel.
Transparent encryption:The encrypted data is completely transparent to legitimate applications and client tools for access. Applications or personnel cannot feel the encryption and decryption process when accessing encrypted data, just like the way plaintext data is accessed. While ensuring data security, it will not change the access habits of applications or personnel.
 Flexible strategy configuration:Different users can authorize different fields of the same table, define different access control policies, and support dual machine hot backup and key export to prevent system damage and inability to decrypt data without keys; Support exporting raw data before encryption to prevent encrypted tables from being damaged and unable to restore the original data.
Flexible strategy configuration:Different users can authorize different fields of the same table, define different access control policies, and support dual machine hot backup and key export to prevent system damage and inability to decrypt data without keys; Support exporting raw data before encryption to prevent encrypted tables from being damaged and unable to restore the original data.
 Excellent database compatibility:Supporting multiple database types such as Oracle, MySQL, PostgreSQL, Dameng, Renmin Jincang, Gaussian DB, and Nanda General Gbase8a, it is one of the database encryption products in the industry that supports the most types of databases. The product adopts encryption plugins and other technologies, which have good database scalability and do not rely on the characteristics of the database itself. It can be extended to support encryption of all relational databases and big data components (Hbase, Hive).
Excellent database compatibility:Supporting multiple database types such as Oracle, MySQL, PostgreSQL, Dameng, Renmin Jincang, Gaussian DB, and Nanda General Gbase8a, it is one of the database encryption products in the industry that supports the most types of databases. The product adopts encryption plugins and other technologies, which have good database scalability and do not rely on the characteristics of the database itself. It can be extended to support encryption of all relational databases and big data components (Hbase, Hive).
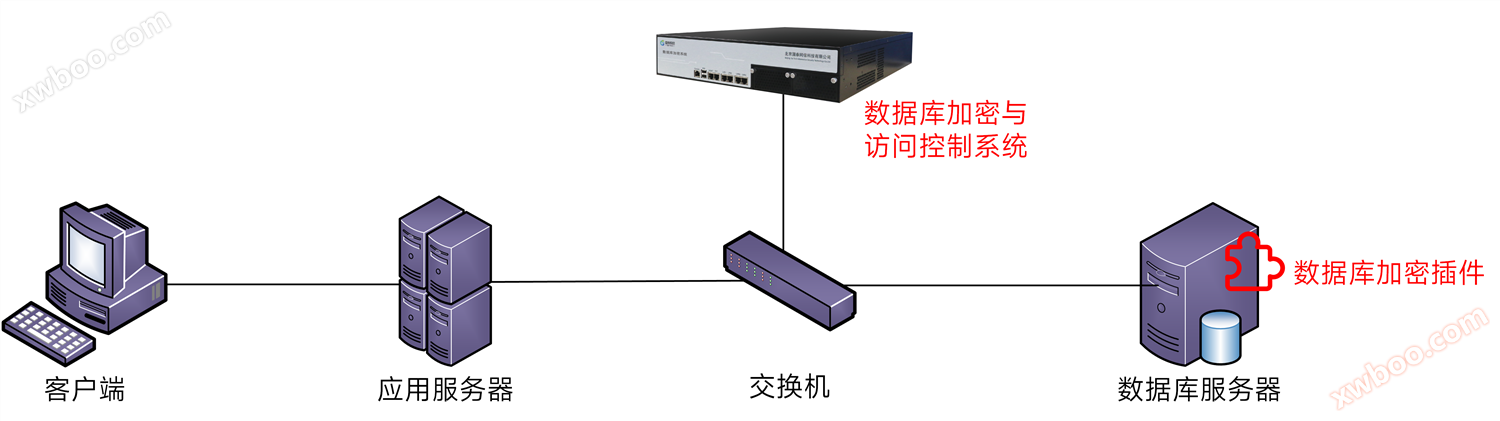
 典型部署
典型部署
The deployment of the database encryption system is simple, using a bypass deployment method that can route to the database server.